ACL on IRB Interface over VXLAN EVPN
Applying ACLs to an Integrated Routing and Bridging (IRB) interface or switchport enables control over packet flow, whether ingress or egress the interface. This capability is essential for maintaining security, managing bandwidth, and ensuring effective routing and bridging.
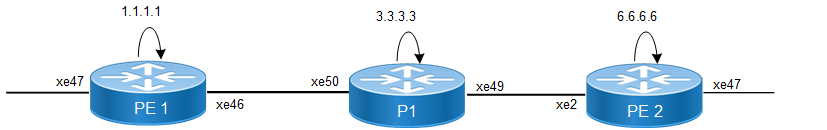
Topology
In this topology, PE1 and PE2 routers have IRB interfaces configured. The IRB interfaces bridge VLAN traffic and route between VLANs, enabling communication between Layer 2 and Layer 3.
ACLs are applied on the IRB interfaces to filter traffic, ensuring only authorized traffic passes through. The P1 router acts as a transit router, forwarding traffic between PE1 and PE2. The P1 router provides core functionality but does not handle IRB interfaces directly.
This configuration ensures that while traffic flows across the network, ACL policies can be enforced at both PE1 and PE2 over the IRB interfaces, securing communication between VLANs and controlling access between external networks
Figure 69. ACL on IRB sample topology
ACLs Configuration on IRB
Perform the following steps to enable EVPN VXLAN on an IRB interface while applying ACLs to control ingress or egress traffic:
The required configuration for ACL on IRB is added in the Configuration section, for the detailed configuration on IRB symmetric and asymmetric refer to the Base Configuration - L2 VxLAN sub-section in theVxLAN-EVPN with IRB section of the OcNOS VXLAN Guide.
| 1. | Enable Hardware Profiles for both IPv4 and IPv6 traffic at the ingress and egress of the interface: |
PE1(config)#hardware-profile filter ingress-ipv6 enable
PE1(config)#hardware-profile filter egress-ipv6 enable
PE1(config)#hardware-profile filter ingress-ipv4 enable
PE1(config)#
| 2. | Enable EVPN VXLAN: |
PE1(config)#nvo vxlan enable
PE1(config)#nvo vxlan irb
PE1(config)#evpn vxlan multihoming enable # Only if multihoming is required| 3. | Configure an anycast MAC address for the gateway in a multihoming scenario, allowing multiple devices to share the same MAC address for redundancy: |
PE1(config)#evpn irb-forwarding anycast-gateway-mac 0000.0000.1111
PE1(config)#
| 4. | Define a MAC VRF for isolating MAC address routing within the EVPN framework: |
PE1(config)#mac vrf vxlan_l2_elan_sh
PE1(config-vrf)#rd 1.1.1.1:100
PE1(config-vrf)#route-target both 100:100
Ensure to provide <RD value> with a value different from PE1’s RD of 1.1.1.1 to maintain proper routing table separation and avoiding conflicts between the two PE devices.
| 5. | Define an IP VRF for routing L3 traffic within the EVPN framework: |
PE1(config)#ip vrf vxlan_l3_elan_sh
PE1(config-vrf)#rd 1111:300
PE1(config-vrf)#route-target both 300:300
PE1(config-vrf)#l3vni 5053
Ensure to provide <rd value> with a value different from PE1’s RD of 1.1.1.1 to maintain proper routing table separation and avoiding conflicts between the two PE devices.
| 6. | Configure EVPN VXLAN for host reachability and specify the IRB interface: |
PE1(config)#nvo vxlan id 50 ingress-replication inner-vid-disabled
PE1(config-nvo)#vxlan host-reachability-protocol evpn-bgp vxlan_l2_elan_mhsh
PE1(config-nvo)#evpn irb50
| 7. | Configure access interface for VLAN encapsulation and map it to the EVPN instance: |
PE1(config)#nvo vxlan access-if port-vlan xe57 3
PE1(config-nvo-acc-if)# map vnid 50
PE1(config-nvo-acc-if)#
| 8. | Create ACL to filter incoming and outgoing traffic: |
PE1(config)#ip access-list 50_DIST_SH
PE1(config-ip-acl)# 100 permit any host 50.1.1.2 any
PE1(config-ip-acl)# 101 deny any host 50.1.1.3 any
PE1(config-ip-acl)# 102 permit any host 50.1.1.4 any
PE1(config-ip-acl)# 103 deny any host 50.1.1.5 any
PE1(config-ip-acl)# default deny-all
PE1(config-ip-acl)#ip access-list 53_DIST_SH
PE1(config-ip-acl)# 100 deny any 53.1.1.0/24 any
PE1(config-ip-acl)# default deny-all
PE1(config-ip-acl)#ipv6 access-list 5000_DIST_SH
PE1(config-ipv6-acl)# 100 permit any 5000::/48 any
PE1(config-ipv6-acl)# default deny-all
PE1(config-ipv6-acl)#
| 9. | Configure the IRB interface with IP addresses, associate it with the VRF, and apply the ACL: |
PE1(config)#interface irb50
PE1(config-irb-if)# ip vrf forwarding vxlan_l3_elan_sh
PE1(config-irb-if)# evpn irb-if-forwarding anycast-gateway-mac
PE1(config-irb-if)# ip address 50.1.1.1/24
PE1(config-irb-if)# ipv6 address 5000::1/48
PE1(config-irb-if)# mtu 9200
PE1(config-irb-if)# ip access-group 50_DIST_SH in
PE1(config-irb-if)# ip access-group 53_DIST_SH out
PE1(config-irb-if)# ipv6 access-group 5000_DIST_SH in
Configuration Snapshot
PE1
PE1#show running-config
!
logging console 5
logging monitor 5
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
!
hardware-profile filter ingress-ipv6 enable
hardware-profile filter egress-ipv6 enable
hardware-profile filter ingress-ipv4 enable
!
bfd interval 3 minrx 3 multiplier 3
!
qos enable
!
hostname PE1
!
ip access-list 50_DIST_SH
100 permit any host 50.1.1.2 any
101 deny any host 50.1.1.3 any
102 permit any host 50.1.1.4 any
103 deny any host 50.1.1.5 any
default deny-all
ip access-list 53_DIST_SH
100 deny any 53.1.1.0/24 any
default deny-all
!
ipv6 access-list 5000_DIST_SH
100 permit any 5000::/48 any
default deny-all
!
vlan database
vlan-reservation 4037-4094
!
nvo vxlan enable
!
nvo vxlan irb
!
evpn esi hold-time 90
!
evpn vxlan multihoming enable
!
ip vrf management
!
ip vrf vxlan_l3_elan_sh
rd 1111:300
route-target both 300:300
l3vni 5053
!
mac vrf vxlan_l2_elan_sh
description vxlan_l2_elan_sh
rd 1.1.1.1:100
route-target both 100:100
!
evpn irb-forwarding anycast-gateway-mac 0000.0000.1111
!
nvo vxlan vtep-ip-global 1.1.1.1
!
nvo vxlan id 50 ingress-replication inner-vid-disabled
vxlan host-reachability-protocol evpn-bgp vxlan_l2_elan_sh
evpn irb50
!
interface eth0
ip vrf forwarding management
ip address dhcp
!
interface irb50
ip vrf forwarding vxlan_l3_elan_sh
evpn irb-if-forwarding anycast-gateway-mac
ip address 50.1.1.1/24
ipv6 address 5000::1/48
mtu 9200
ip access-group 50_DIST_SH in
ip access-group 53_DIST_SH out
ipv6 access-group 5000_DIST_SH in
!
interface lo
ip address 127.0.0.1/8
ip address 1.1.1.1/32 secondary
ipv6 address ::1/128
!
interface xe46
description network_to_spine1
load-interval 30
ip address 11.1.1.1/24
mtu 9200
!
interface xe47
switchport
load-interval 30
mtu 9200
!
exit
!
router ospf 1
ospf router-id 1.1.1.1
bfd all-interfaces
network 1.1.1.1/32 area 0.0.0.0
network 11.1.1.0/24 area 0.0.0.0
!
router bgp 1
bgp router-id 1.1.1.1
neighbor 6.6.6.6 remote-as 1
neighbor 6.6.6.6 update-source lo
!
address-family ipv4 unicast
max-paths ibgp 2
redistribute connected
exit-address-family
!
address-family l2vpn evpn
neighbor 6.6.6.6 activate
exit-address-family
!
address-family ipv4 vrf vxlan_l3_elan_sh
max-paths ibgp 2
redistribute connected
exit-address-family
!
address-family ipv6 vrf vxlan_l3_elan_sh
max-paths ibgp 2
redistribute connected
exit-address-family
!
exit
!
nvo vxlan access-if port-vlan xe47 3
map vnid 50
!
!
endPE2
PE2#show running-config
!
logging console 5
logging monitor 5
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
!
hardware-profile filter ingress-ipv6 enable
hardware-profile filter egress-ipv6 enable
hardware-profile filter bfd-group disable
hardware-profile filter ingress-ipv4 enable
!
bfd interval 3 minrx 3 multiplier 3
!
qos enable
!
hostname PE2
!
ip access-list 53_DIST_SH
100 permit any 53.1.1.0/24 any
default deny-all
!
ipv6 access-list 5301_DIST_SH
100 deny any 5301::/48 any
default permit-all
!
vlan database
vlan-reservation 4000-4094
vlan 50 bridge 1 state enable
vlan 60 bridge 1 state enable
vlan 100-300 bridge 1 state enable
!
nvo vxlan enable
!
nvo vxlan irb
!
evpn vxlan multihoming enable
!
ip vrf management
!
ip vrf vxlan_l3_elan_sh
rd 6666:300
route-target both 300:300
l3vni 5053
!
mac vrf vxlan_l2_elan_sh2
description vxlan_l2_elan_sh
rd 6.6.6.6:200
route-target both 200:200
!
evpn irb-forwarding anycast-gateway-mac 0000.0000.1111
!
nvo vxlan vtep-ip-global 6.6.6.6
!
nvo vxlan id 53 ingress-replication inner-vid-disabled
vxlan host-reachability-protocol evpn-bgp vxlan_l2_elan_sh2
evpn irb53
!
interface eth0
ip vrf forwarding management
ip address dhcp
!
interface irb53
ip vrf forwarding vxlan_l3_elan_sh
evpn irb-if-forwarding anycast-gateway-mac
ip address 53.1.1.1/24
ipv6 address 5301::1/48
mtu 9200
ip access-group 53_DIST_SH in
ipv6 access-group 5301_DIST_SH in
!
interface lo
ip address 127.0.0.1/8
ip address 6.6.6.6/32 secondary
ipv6 address ::1/128
!
interface xe2
description network_to_spine1
load-interval 30
ip address 17.1.1.1/24
mtu 9200
!
interface xe47
switchport
load-interval 30
mtu 9200
!
!
exit
!
router ospf 1
ospf router-id 6.6.6.6
bfd all-interfaces
network 6.6.6.6/32 area 0.0.0.0
network 17.1.1.0/24 area 0.0.0.0
!
router bgp 1
bgp router-id 6.6.6.6
neighbor 1.1.1.1 remote-as 1
neighbor 1.1.1.1 update-source lo
!
address-family l2vpn evpn
neighbor 1.1.1.1 activate
exit-address-family
!
address-family ipv4 vrf vxlan_l3_elan_sh
max-paths ibgp 2
redistribute connected
exit-address-family
!
address-family ipv6 vrf vxlan_l3_elan_sh
max-paths ibgp 2
redistribute connected
exit-address-family
!
exit
!
nvo vxlan access-if port-vlan xe47 9
map vnid 53
!
!
end
P1
P#show running-config
!
logging console 5
logging monitor 5
snmp-server enable traps link linkDown
snmp-server enable traps link linkUp
!
qos enable
!
hostname P
!
interface lo
ip address 127.0.0.1/8
ip address 1.1.1.1/32 secondary
ipv6 address ::1/128
!
interface xe49
load-interval 30
ip address 17.1.1.2/24
mtu 9200
!
interface xe50
load-interval 30
ip address 11.1.1.2/24
mtu 9200
!
exit
!
router ospf 1
ospf router-id 3.3.3.3
bfd all-interfaces
network 3.3.3.3/32 area 0.0.0.0
network 11.1.1.0/24 area 0.0.0.0
network 17.1.1.0/24 area 0.0.0.0
!
end
Validation
Verify that after applying ACL, traffic drop/permit is seen as per policy and verify acl counters are increased accordingly:
PE1#show interface counters rate mbps
+-------------------+--------------+-------------+--------------+-------------+
| Interface | Rx mbps | Rx pps | Tx mbps | Tx pps |
+-------------------+--------------+-------------+--------------+-------------+
xe46 499.46 13304 239.42 6387
xe47 398.19 10674 0.00 0
PE1#
PE1#show access-lists
IP access list 50_DIST_SH
100 permit any host 50.1.1.2 any [match=485136]
101 deny any host 50.1.1.3 any [match=485135]
102 permit any host 50.1.1.4 any [match=485134]
103 deny any host 50.1.1.5 any [match=485132]
default deny-all [match=2910786]
IP access list 53_DIST_SH
100 deny any 53.1.1.0/24 any [match=4153575]
default deny-all
IPv6 access list 5000_DIST_SH
100 permit any 5000::/48 any [match=4719226]
268435453 permit icmpv6 any any [match=55]
default deny-all